WhoTracks.Me
The Ultimate Guide To Third-Party Cookies
Key Points:
- Third-party cookies are the cause of multiple privacy and security issues on the web.
- Despite the cookie spec writers recommending against it, all major browsers ended up allowing third-party cookies by default.
- Several major sites and services, including those from Microsoft and Google, fail badly when third-party cookies are blocked.
- Ghostery defuses the privacy issues of third-party cookies by blocking them, while preventing the breakage issues caused by developers assuming a cookie free-for-all.

Third-Party Cookies
Cookies are a fundamental browser technology which enables state to be kept between browser and servers over the normally stateless HTTP protocol.
Cookies enable sites to remember your login, what you've put in your shopping cart, and allow a site to remember language or currency preferences.
These features enable the sites you're visiting, 'first parties', to improve your experience and provide some content behind authentication, only accessible to you. However, browsers also, by default, send cookies to any third-parties embedded by the site operators.
In some cases these can be used to allow third-party widgets, such as Disqus comments, to automatically log you in to embedded content in the page. But it also enables these third-parties to track your browsing across the web.
Privacy Risk
Allowing cookies to third-parties opens up a privacy hole in your browser.
On many sites, just visiting a page will set cookies for over 50 different third-party domains. Each of these are setting cookies so they can correlate requests coming from your browser over days, months, or even years.
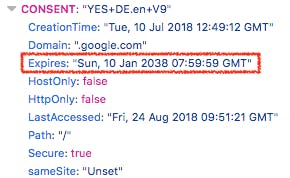
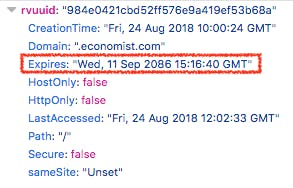
For example, when you visit any page with a Facebook widget (or visit Facebook itself), they will set a cookie which will only expire in 2 years time. Some google.com cookies expire in 20 years.
The facebook.com and google.com domains are present as a third-party to 24% and 30% of page loads on the web respectively, allowing these services to tracker this proportion of the average user's web browsing history.
Security Risk
Third-party cookies also represent a security risk to you.
Cross-site request forgery (CSRF) attacks are based on the idea that I can make a third-party request to a site that the browser has previously authenticated with, and the browser will send the credentials with the request. If browsers did not allow third-party cookies these attacks would be much harder to exploit than they currently are.
These kinds of attacks have been around for over 15 years, and methods to mitigate them are still being proposed, while browser-side protection, such as first-party isolation, have very limited distribution.
Furthermore, the use-cases which legitimately use third-party cookies, like Single-Sign-On portals, or third-party authentication mechanisms, have alternatives which do not require cookies.
Sites using a centralized authentication domain can obtain authentication tokens via first-party redirects, and OAuth can be used to log in to sites using third-party credentials.
(Note that both of these methods also have some privacy issues. First-party redirection has been exploited for user tracking, and OAuth dialogs can trick users into granting many more permissions than they actually need).
These mechanisms have the added bonus of transparency and implied consent: When a user logs in with Facebook on a site, the user is actively allowing this connection between the site and Facebook to proceed.
How Third-Party Cookies work
Third-party cookies are cookies that are tracked by websites other than the one you are currently visiting. Advertisers collect user data and track your browsing habits through third-party cookies.
For instance, let's say you were shopping online for Nike shoes. You browsed a few retail sites, compared styles and prices, but didn't make a purchase
A few days later, Nike ads start popping up on unrelated websites you visit. This happens because the shoe sites placed cookies in your browser, allowing them to target ads based on your shopping behavior.
Even when you close those initial retail tabs, the cookies remain, compiling data across your sessions. So even though you were just researching, brands will serve ads and follow you around the web.
Most browsers don't automatically delete third-party cookies when you quit them. You usually have to manually clear your cookies to stop this "crumb trail" of your web history.
Are Third-Party cookies actually useful?
Third-party cookies can serve some legitimate purposes, though they also enable extensive user tracking and profiling. In the past, some potential benefits of third-party cookies were used for:
- Fraud prevention: Services may use them to detect fraudulent activity across different sites. For example, if the same device is making lots of account signups from different locations.
- Single sign-on: They can enable users to sign in once with a third-party service like Facebook or Google and then access other sites without having to sign in again.
- Personalization: They allow sites to coordinate with third-party services to remember user preferences, customizations, etc. For example, remembering items in a shopping cart across sites.
However, these services no longer require third-party cookies to function.
Most third-party cookies track users to serve targeted, behavioral ads without meaningful user consent. They provide advertisers extensive data about user behaviors, demographics, interests, and more.
Once they’re aware of this activity, many people desire to block third-party cookies to mitigate one way that sites collect user data.
Some sites have returned to privacy-focused alternatives, like contextually-relevant ads based solely on page content rather than user profiles, but they are a small minority. Behavioral ads powered by third-party cookies remain dominant for now due to the substantial profits they generate.
Why Third-Party cookies exist
Again, why do we have third-party cookies? The original 1997 RFC Specification of the cookie standard proposed that third-party cookies should not be allowed on privacy grounds:
This restriction prevents a malicious service author from using unverifiable transactions to induce a user agent to start or continue a session with a server in a different domain. The starting or continuation of such sessions could be contrary to the privacy expectations of the user, and could also be a security problem.
and browsers should have this setting by default:
User agents may offer configurable options that allow the user agent, or any autonomous programs that the user agent executes, to ignore the above rule, so long as these override options default to "off".
However, these recommendations were not implemented by browser developers at that time, and the default of 'allow all cookies' has remained since then.
Currently, almost all major browsers have a default to allow all cookies. The two major exceptions are Safari, Firefox, and Brave, who isolate or block third-party content.
Historically, adding more privacy protections to browsers has been a struggle.
For instance, Mozilla also previously attempted to change Firefox's default handling of third-party cookies in 2013, but pressure from the ad industry led to a U-turn before these changes went live.
The failure of browsers to handle third-party cookie tracking has arguably led to the increase in ad blocker usage since then.
How to tell if a website uses Third-Party cookies?
Determining whether a website utilizes third-party cookies is possible on all major browsers. Some browsers now block third-party cookies or confine them by default, like Safari and Firefox.
Chrome / Edge / Opera
1) Right-click on the page and choose Inspect. You can also press F12 to open Developer Tools instead.
2) In Developer Tools, choose the Application tab.
3) On the left, double-click the Cookies section to expand that section.
Safari
Note: Safari already blocks third-party cookies by default, but you can look at other site data.
- Open Safari and click on the Safari menu at the top left corner of the screen.
- Select Settings from the menu that appears.
- Click on the Privacy tab.
- Click the Manage Website Data... button.
- To get rid of specific cookies, select one or more websites, then click Remove. To get rid of all cookies, choose Remove All and then Remove Now. (Note this affects all website data, not just cookies.)
Firefox
- Click the shield icon in the URL bar and select Cross-Site Tracking Cookies.
Ghostery Private Browser
- Right-click on the page and choose Inspect.
- Select the Storage tab.
- On the left site, look under Cookies.
Moving away from third-party cookies
In 2015 Cliqz, the former search engine, browser, and company behind Ghostery, released an anti-tracking technology which aggressively blocks third-party cookies.
Third-party cookies are blocked unless certain heuristics are triggered. These heuristics aim to mitigate common cases where cookie blocking breaks workflows, but also require user action to trigger.
A Facebook button can be loaded without cookies, but if the user then clicks on it, there is an implied consent to allow the cookies in this case. This method blocks 97% of third-party cookies, with minimal breakage of pages.
In December 2017, this technology was included in the Ghostery 8 release. This increased the number of users with this aggressive cookie blocking behavior and this increased exposure also highlighted more cases where cookie blocking causes problems for websites.
In many cases it may not be surprising that developers have not considered or tested the possibility of third-party cookies being blocked. What surprised us though, is that this is so pervasive that the biggest players fail to handle cookies properly, in some cases causing critical bugs.
At present, if you browse the web with third-party cookies disabled, you may come across issues logging in and making payments.
Pay with your Cookies
It is common practice for E-Commerce sites to embed payment systems from third-party vendors, such as Paypal, on their checkout pages. Such widgets should not require third-party cookies— usually the user can be redirected to pay at the payment provider's site.
This method is preferable, as it reduces the chances of phishing: loading the payment page as a first party will make the url and certificate status visible, and only prompting users to enter payment information on the first party site is also good practice.
Please let me track your tracking opt-out
Following GDPR, websites using third-party services which collect data about users acquire consent for this, as well as provide a reasonable way of opting-out of data collection and processing.
While many publishers have converged on a solution which gathers consent as a first-party cookie which can then be passed to third-parties, others still rely on an older system of setting opt-out cookies for each vendor. Obviously, if third-party cookies are blocked, this mechanism will not work.
In this case, users with third-party cookies disabled will be denied their right to opt-out (though blocking these cookies will effectively prevent a large proportion of cookie tracking).
Third-party vendors may say that this mechanism is required in order to remember a user's consent settings. However, previous attempts to allow browsers to convey tracking consent explicitly to servers, via the 'Do Not Track' standard were killed by the same vendors collectively saying they would ignore this signal.
Conclusion
When the idea of cookies was first proposed, the standard writers were concerned about the privacy implications of allow third-party cookies, and specified that browser vendors should disable them by default.
Fast-forward 20 years and the majority of browsers on the web still allow all third-party cookies. The result of this are significant challenges to protect against cross-site request forgery, with countless sites and accounts compromised along the way, and pervasive privacy invasion in the form of cross-site tracking of users.
We argue that we should aim to return to a web where third-party cookies are blocked by default, and are making that possible for users of our anti-tracking technology in Ghostery
However, this is made difficult by the prevailing assumption that cookies are a free-for-all, making many sites fail to function properly in this environment. In this regard we are constantly improving heuristics to mitigate the breakage issues we do find.
For users, getting control over which cookies your browser sends out, and to whom, is a key part of protecting privacy online, but also something that is not universally recognised by browser privacy tools.
Most adblockers, for example, do nothing to the cookies of third-party requests which are not on their blocklists. More adoption of the kind of cookie blocking that Ghostery does help us to achieve this critical mass, and push more websites to ensure that their services still work correctly for users who chose more private browser configurations.
Developers have a part to play here too. By building services which do not require third-party cookies, or at least continue to function without them, it becomes easier for users to turn off third-party cookies, and the web becomes more privacy-friendly.
As we have seen in this article, even the biggest tech companies are currently failing at this, but this seems to be more due to a lack of awareness, than any difficulty in implementation.

